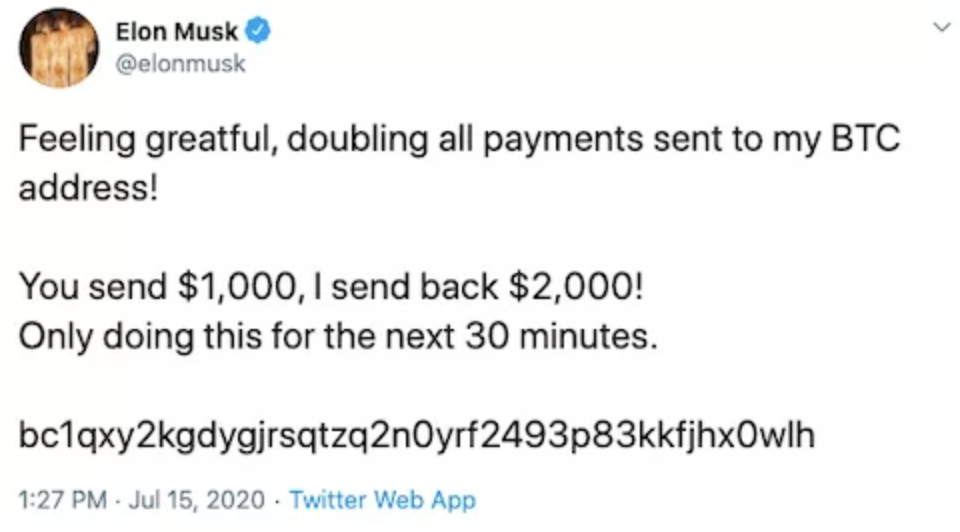
What happened: Hackers accessed a slew of Twitter accounts to sell; took control of high-profile accounts to Tweet links to a Bitcoin scam.
In a recent blog post, Twitter admitted that its platform was hacked last Wednesday, July 15, 2020. Twitter alleged hackers engaged in a “social engineering scheme” to access its internal tools. Twitter defined “social engineering” as “the intentional manipulation of people into performing certain actions and giving out their personal information.”
Ultimately, hackers accessed 130 Twitter accounts. The hackers were able to reset the password for 45 accounts; they then logged into those accounts and Tweeted out cryptocurrency "bitcoin" scams. The hacking scheme escalated just before 3:30 p.m. on July 15, 2020. According to a New York Times’ investigation, certain cryptocurrency company elites’ accounts began asking for Bitcoin donations to a website called “cryptoforhealth.” The Bitcoin wallet set up to receive the donations was none other than the wallet “Kirk” had been using all day. “Kirk” then started tweeting out links from celebrities’ and tech giants’ accounts which told users to send money to a Bitcoin account and in return, the amount would be doubled.
According to one investigation by Krebs, the Bitcoin account processed 383 transactions; according to NYT, 518 transactions were processed worldwide. It wasn’t until around 6 p.m. when Twitter put a stop to the scam messages. Twitter’s blog post stated: “We’re embarrassed, we’re disappointed, and more than anything, we’re sorry.” Once the hacks were detected, Twitter “secured and revoked access to internal systems,” restricted the functionality of many Twitter accounts – preventing Tweeting and password changes, and locked accounts when there was a recent password change.
What was accessed?
Twitter assured its users for all but the 130 hacked accounts, no personal information was compromised. However, it is likely the hackers saw the users’ personal information, like phone numbers, email addresses. For the 45 accounts that were taken over by the hackers, more information was compromised – but Twitter did not state what information that could be. The hackers downloaded user's information, such as a summary of the user’s activity and account details, for eight accounts. It is unclear which eight accounts were affected at this time.
Investigators are trying to identify the hackers – foreign state interference is not suspected.
Investigators are trying to figure out if a Twitter employee was involved or whether, as Twitter claimed, the hacking was orchestrated by social engineering, where one individual posed as a trusted employee to gain credentials and account access. The Federal Bureau of Investigation said, "the accounts appear to have been compromised in order to perpetuate cryptocurrency fraud.” U.S. senators have demanded Twitter submit a brief by July 23, 2020. New York Governor Andrew Cuomo announced the state will conduct a full investigation.
According to an exclusive New York Times interview with four of the culprits, the organized hacking scheme was not politically motivated, despite targeting some political and corporate elites. The New York Times verified the hackers’ identities – “lol,” “ever so anxious,” and two others – through matching their social media and cryptocurrency accounts. The hackers also provided photos of their chat logs. Another source Krebs identified another key player in the Twitter Hack “PlugWalkJoe.” Investigators have confirmed some of the information relayed to the New York Times’ exclusive interview. “lol” is a 20-something, living on the United States’ West Coast. “ever so anxious” is 19, living with his mother in the South of England. Both are well-known gamers on OGusers.com. “PlugWalkJoe,” whose name is Joseph O’Connor, is 21, British, and was in Spain when the Twitter hack scheme started. Mr. O’Connor insists he played no part in Wednesday’s events. Alternatively, “Kirk” was unknown before Wednesday’s Twitter Hack – and his real identity is still under investigation.
The scheme began with messages the previous Tuesday night between two hackers, “Kirk” and “lol.” “Kirk” reached out to “lol,” alleging he worked at Twitter and demonstrated he could take control of valuable Twitter accounts. The hackers claim they were not part of a foreign interference plot – they are a bunch of young people, one still living with his mom – obsessed with owning early or unusual user names having one letter or number, such as @y or @6. But “lol” told the New York Times he suspected “Kirk” did not work at Twitter because he was “too willing to damage the company.”
Regardless, “Kirk” could take control of almost any Twitter account, including former President Obama, former Vice President and the Democratic presidential nominee, Joseph R. Biden, Elon Musk, and other celebrities. The BBC reported that other elites’ accounts were hacked too, like Bill Gates, Kim Kardashian, Kanye West, Apple, and Uber. Another source Krebs adds Jeff Bezos, former New York Mayor Michael Bloomberg, and Warren Buffett to the list.
Prestige is King – Four hackers were inspired by an obsession with “OG user names.”
According to the hackers, “Kirk” directed the group’s efforts. However, two hackers, “lol” and “ever so anxious,” told the New York Times they sought the prestige of owning an original user name. The two claim they only helped “Kirk” by facilitating the purchases and takeovers of OG, or “original gangster,” user names earlier Wednesday. In their interview, the four hackers insisted they parted ways with “Kirk” before he started taking over higher-profile accounts. In the online gaming world, certain user names associated with the launch of a new online platform – so-called OG user names – are highly desired. These prestigious user names are snagged by the earliest users of the new platform. Many latecomers to the platform want the credibility of the OG user names, and will often pay big bucks to get one.
Wednesday’s hacking scheme began with a plan to commandeer and sell OG user names. “Kirk” asked “lol” and “ever so anxious” to act as middlemen for the sale of some Twitter OG user names. “Kirk” promised the other two would get a cut of each transaction they secured. For example, the first “deal” “lol” brokered included a person offering $1500 in Bitcoin for the “@y” user name. The group posted an advertisement on OGusers.com and customers poured in. The group sold user names like @b, @dark, @l, @R9, @vague, @w, @6, and @50. One buyer, and possible culprit, “PlugWalkJoe,” bought the “@6” user name from “ever so anxious,” while “ever so anxious” commandeered the user name “@anxious.” Nearly all the transactions that occurred in relation to the Twitter Hack went into one Bitcoin wallet, predominately used by “Kirk” throughout the day.
Election Day 2020 Concerns
Because high-profile politicians’ accounts were compromised in Wednesday’s Twitter Hack, many express concerns about potential disinformation campaigns closer to November 3rd. These concerns are exacerbated by the fact Twitter did not detect the hacking scheme for hours after the hacks started. While U.S. and state government officials have sought to protect voting systems against potential hacking, Wednesday’s chaos has shown us that efforts to protect the security of the upcoming presidential election might need renewed attention. The investigations into the Twitter Hack are still ongoing, and many details remain unclear.
– written by Allison Hedrick